Last updated: 4 June 2025
As online threats grow more sophisticated, WordPress security & data privacy are paramount. However, there's a subtle yet significant privacy vulnerability that many WordPress site owners overlook.
TL;DR:
- Username enumeration exposes user identifiers, often via author archives or the REST API.
- Attackers can use this information for brute-force attacks or phishing campaigns.
- Many users use email addresses as usernames, increasing privacy risks.
- Exposing usernames compromises both site security and user confidentiality.
- Prevent it by installing a reputable security plugin like Wordfence.
This vulnerability lies in the exposure of wp-admin usernames, a default behaviour of the WordPress REST API. Taking advantage of this is known as "Username Enumeration".
In this article we will start by diving into what Username Enumeration is, why it might be a concern for you, and how can you prevent it. We will also update this article in the future with other scenarios that are worth looking into. But for now, lets start off with Username Enumeration.
Disclaimer: This article discusses techniques for enhancing privacy and security on WordPress sites, including methods that might be considered 'security by obscurity'. It's important to note that while obscuring information like author usernames can add a layer of protection, it should not be the sole security strategy. Effective security involves multiple layers of protection, and relying solely on obscurity is not a recommended practice. Always complement these techniques with robust security measures for comprehensive protection.
What is WordPress Username Enumeration?
Username enumeration refers to a security vulnerability where an attacker can easily discover user usernames through the site. This usually occurs due to certain features or plugins that display user information publicly or through predictable patterns. For instance, error messages during the login process can reveal if a username exists. Knowing usernames gives attackers a significant head start in attempting unauthorised access, as they only need to figure out the passwords.
Proof of Concept:
The core of the problem is that the WordPress REST API, by default, allows anyone to view a list of users registered on a site. This information can be accessed simply by appending the following to the end of your website's URL: /wp-json/wp/v2/users
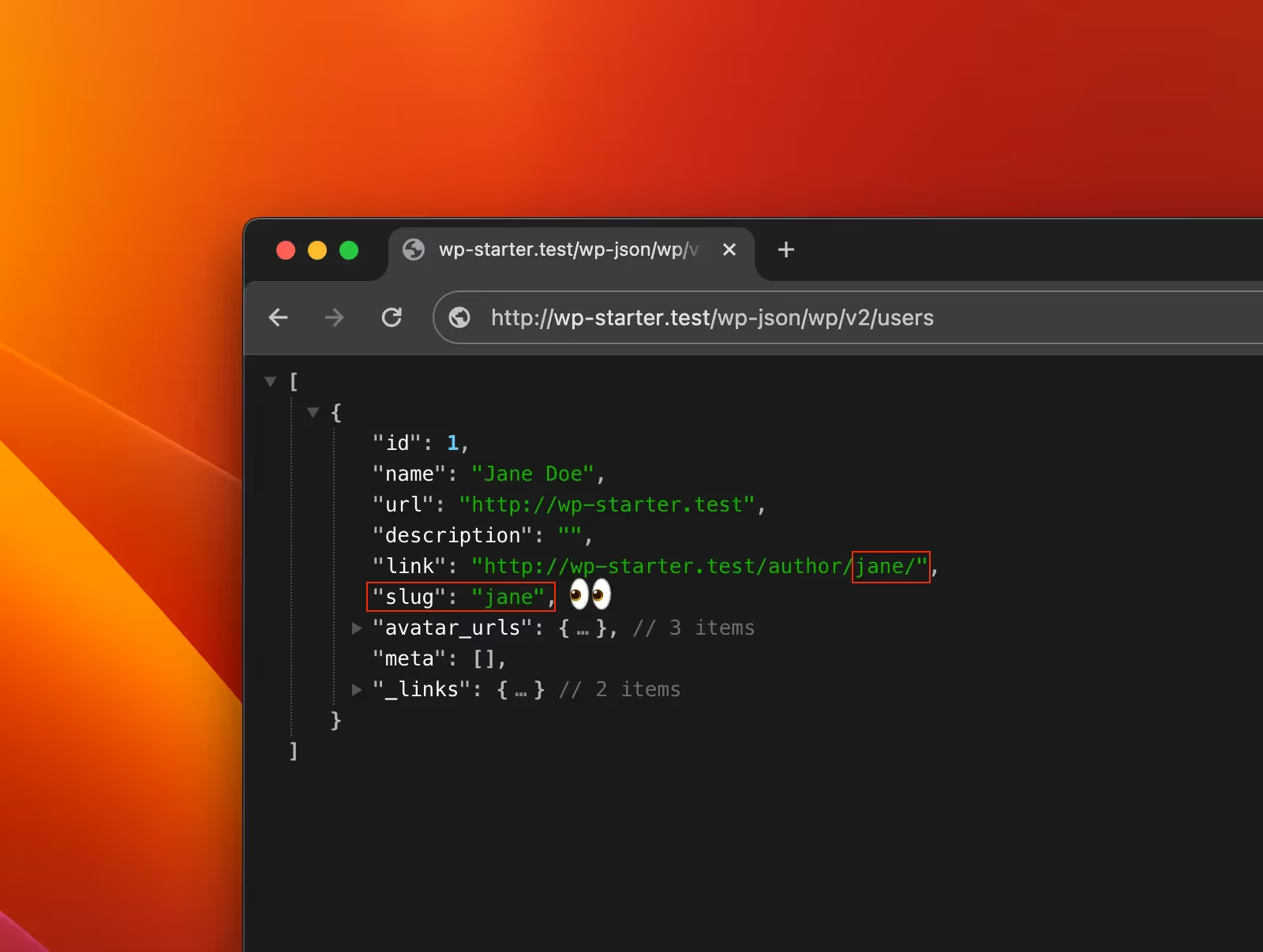
PS: To clarify what is being exposed here is technically the users 'user_nicename' data and not the 'user_login' (username) data however in majority of the cases, those 2 values are the same because that is how WordPress sets it up by default (user_nicename is the slug value of 'user_login') and it cannot be changed within the UI.
Why is WordPress Username Enumeration a Problem?
TL;DR:
- Exposes personally identifiable information (PII)
- Enables targeted brute-force or phishing attacks
- Increases risk when usernames are email addresses
It might seem harmless to expose usernames. But doing so can have serious consequences for both privacy and security.
When attackers obtain admin usernames, they don't just gain a foothold for potential security breaches like brute force attacks; they also infringe upon the privacy of your site administrators. Having this personal information makes it easier for attackers to break in (albeit, only one piece of the puzzle), compromising not only the security but also the confidentiality of sensitive areas on your site.
In many cases, users - especially administrators - may use their email address as their username. This further increases the risk by exposing a piece of personally identifiable information (PII) that can be leveraged in phishing attempts or brute-force attacks. Protecting usernames, therefore, isn’t just a best practice - it’s a critical step in safeguarding your site’s security and your users’ privacy.
How do I prevent Username Enumeration?
TL;DR:
- Install a security plugin like WordFence
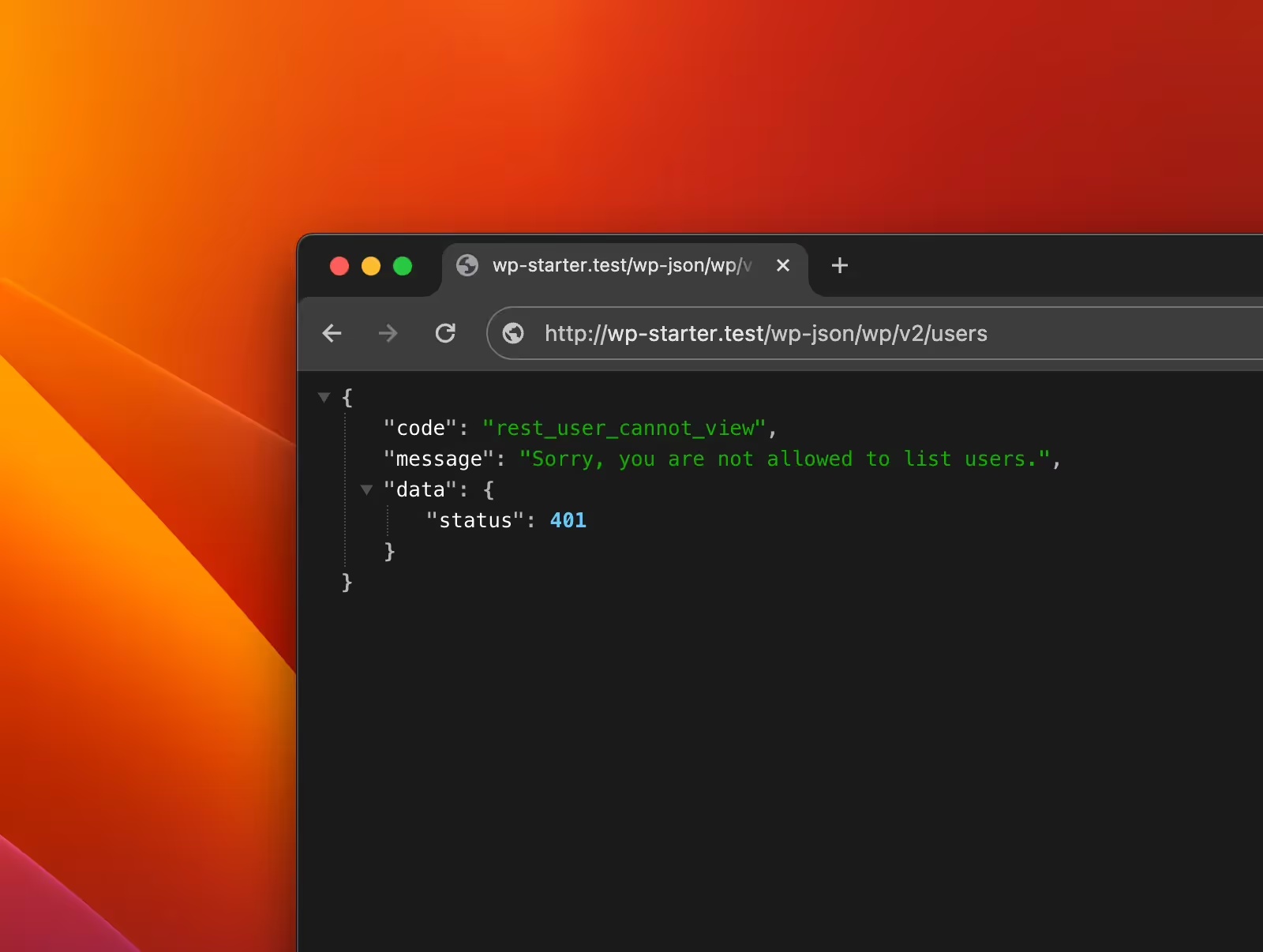
The good news is that addressing this vulnerability is straightforward. One of the many effective 'no-code' solutions to stop user enumeration is to install a plugin like WordFence. By default, this security plugin provides protection against attackers trying to enumerate usernames. It's a simple yet effective measure to bolster the security of your WordPress site.
WordPress Partner Agency
If you're seeking a reliable and experienced WordPress Web Design Agency, consider partnering with us. We are passionate about delivering secure, optimised, and visually stunning custom WordPress websites.

.webp)
